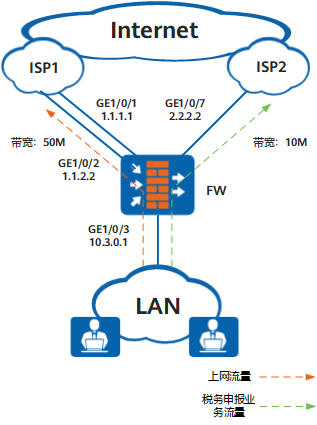
通过配置根据链路优先级主备备份,FW可以在主接口链路故障时,使用备份接口链路转发流量,提高传输的可靠性。
配置思路
由于企业希望优先使用ISP1链路,所以全局智能选路方式可以设置为根据链路优先级主备备份,指定2条ISP1链路的优先级均为2,ISP2链路的优先级为1。而税务申报业务需要优先使用ISP2链路,所以要针对税务申报应用配置策略路由智能选路,选路方式也是根据链路优先级主备备份,并指定ISP2链路的优先级为2,2条ISP1链路的优先级均为1。为了保证主接口链路故障时,FW可以使用备份接口链路转发流量,还需要配置健康检查功能。
-
配置全局选路策略。配置智能选路方式为根据链路优先级主备备份,接口GE1/0/1和GE1/0/2加入一个接口组ifgrp1,并和接口GE1/0/7一起作为智能选路成员。分别为接口组ifgrp1和接口GE1/0/7设置优先级,接口GE1/0/1和GE1/0/2的优先级即等于接口组ifgrp1的优先级。
-
配置策略路由智能选路。为税务申报应用新建一条策略路由,配置智能选路方式为根据链路优先级主备备份,分别为接口组ifgrp1和接口GE1/0/7设置优先级。

本例着重介绍智能选路相关的配置,其余配置如NAT请根据实际组网进行配置。
操作步骤
- 可选:开启健康检查功能,并为ISP1和ISP2链路分别新建一个健康检查。假设ISP1网络的目的地址网段为3.3.10.0/24,ISP2网络的目的地址网段为9.9.20.0/24。
<FW> system-view [FW] healthcheck enable [FW] healthcheck name isp1_health_01 [FW-healthcheck-isp1_health_01] destination 3.3.10.10 interface GigabitEthernet 1/0/1 protocol tcp-simple destination-port 10001 [FW-healthcheck-isp1_health_01] destination 3.3.10.11 interface GigabitEthernet 1/0/1 protocol tcp-simple destination-port 10002 [FW-healthcheck-isp1_health_01] quit [FW] healthcheck name isp1_health_02 [FW-healthcheck-isp1_health_02] destination 3.3.10.12 interface GigabitEthernet 1/0/2 protocol tcp-simple destination-port 10001 [FW-healthcheck-isp1_health_02] destination 3.3.10.13 interface GigabitEthernet 1/0/2 protocol tcp-simple destination-port 10002 [FW-healthcheck-isp1_health_02] quit [FW] healthcheck name isp2_health [FW-healthcheck-isp2_health] destination 9.9.20.20 interface GigabitEthernet 1/0/7 protocol tcp-simple destination-port 10003 [FW-healthcheck-isp2_health] destination 9.9.20.21 interface GigabitEthernet 1/0/7 protocol tcp-simple destination-port 10004 [FW-healthcheck-isp2_health] quit

此处假设3.3.10.10~3.3.10.13和9.9.20.20、9.9.20.21分别为ISP1和ISP2网络中已知的设备地址。
如果健康检查配置完后,状态一直为down,请检查健康检查的配置。
对于V500R001C80之前的版本,需要在FW上配置对应的安全策略,允许FW向目的设备发送健康检查探测报文。对于V500R001C80及之后的版本,健康检查的探测报文不受安全策略控制,默认放行,无需配置相应安全策略。
- 配置接口的IP地址和网关地址,配置接口所在链路的带宽,并应用对应的健康检查。
[FW] interface GigabitEthernet 1/0/1 [FW-GigabitEthernet1/0/1] ip address 1.1.1.1 255.255.255.0 [FW-GigabitEthernet1/0/1] gateway 1.1.1.254 [FW-GigabitEthernet1/0/1] bandwidth ingress 50000 [FW-GigabitEthernet1/0/1] bandwidth egress 50000 [FW-GigabitEthernet1/0/1] healthcheck isp1_health_01 [FW-GigabitEthernet1/0/1] quit [FW] interface GigabitEthernet 1/0/2 [FW-GigabitEthernet1/0/2] ip address 1.1.2.2 255.255.255.0 [FW-GigabitEthernet1/0/2] gateway 1.1.2.254 [FW-GigabitEthernet1/0/2] bandwidth ingress 50000 [FW-GigabitEthernet1/0/2] bandwidth egress 50000 [FW-GigabitEthernet1/0/2] healthcheck isp1_health_02 [FW-GigabitEthernet1/0/2] quit [FW] interface GigabitEthernet 1/0/3 [FW-GigabitEthernet1/0/3] ip address 10.3.0.1 255.255.255.0 [FW-GigabitEthernet1/0/3] quit [FW] interface GigabitEthernet 1/0/7 [FW-GigabitEthernet1/0/7] ip address 2.2.2.2 255.255.255.0 [FW-GigabitEthernet1/0/7] gateway 2.2.2.254 [FW-GigabitEthernet1/0/7] bandwidth ingress 10000 [FW-GigabitEthernet1/0/7] bandwidth egress 10000 [FW-GigabitEthernet1/0/7] healthcheck isp2_health [FW-GigabitEthernet1/0/7] quit
- 新建接口组ifgrp1,并将接口GE1/0/1和GE1/0/2加入接口组。
[FW] interface-group 1 name ifgrp1 [FW-interface-group-1] add interface GigabitEthernet 1/0/1 [FW-interface-group-1] add interface GigabitEthernet 1/0/2 [FW-interface-group-1] quit
- 配置全局选路策略,流量根据链路优先级主备备份。
[FW] multi-interface [FW-multi-inter] mode priority-of-userdefine [FW-multi-inter] add interface-group ifgrp1 priority 2 [FW-multi-inter] add interface GigabitEthernet1/0/7 [FW-multi-inter] quit
- 自定义税务申报应用,假设应用服务器的IP地址为8.8.8.8,端口为20001。
[FW] sa [FW-sa] user-defined-application name UD_tax_system [FW-sa-user-defined-app-UD_tax_system] rule name 1 [FW-sa-user-defined-app-UD_tax_system-rule-1] ip-address 8.8.8.8 32 [FW-sa-user-defined-app-UD_tax_system-rule-1] port 20001 [FW-sa-user-defined-app-UD_tax_system-rule-1] quit [FW-sa-user-defined-app-UD_tax_system] quit [FW-sa] quit
- 为税务申报应用配置策略路由智能选路,流量根据链路优先级主备备份。
[FW] policy-based-route [FW-policy-pbr] rule name tax_system [FW-policy-pbr-rule-tax_system] source-zone trust [FW-policy-pbr-rule-tax_system] application app UD_tax_system [FW-policy-pbr-rule-tax_system] action pbr egress-interface multi-interface [FW-policy-pbr-rule-tax_system-multi-inter] mode priority-of-userdefine [FW-policy-pbr-rule-tax_system-multi-inter] add interface-group ifgrp1 [FW-policy-pbr-rule-tax_system-multi-inter] add interface GigabitEthernet1/0/7 priority 2 [FW-policy-pbr-rule-tax_system-multi-inter] quit [FW-policy-pbr] quit
- 将接口加入安全区域。
[FW] firewall zone trust [FW-zone-trust] add interface GigabitEthernet 1/0/3 [FW-zone-trust] quit [FW] firewall zone untrust [FW-zone-untrust] add interface GigabitEthernet 1/0/1 [FW-zone-untrust] add interface GigabitEthernet 1/0/2 [FW-zone-untrust] add interface GigabitEthernet 1/0/7 [FW-zone-untrust] quit
- 配置Local到Untrust区域的安全策略,允许FW向目的设备发送相应的健康检查探测报文。

对于V500R001C80之前的版本,需要在FW上配置对应的安全策略,允许FW向目的设备发送健康检查探测报文。对于V500R001C80及之后的版本,健康检查的探测报文不受安全策略控制,默认放行,无需配置相应安全策略。
[FW] security-policy [FW-policy-security] rule name policy_sec_local_untrust [FW-policy-security-rule-policy_sec_local_untrust] source-zone local [FW-policy-security-rule-policy_sec_local_untrust] destination-zone untrust [FW-policy-security-rule-policy_sec_local_untrust] destination-address 3.3.10.10 32 [FW-policy-security-rule-policy_sec_local_untrust] destination-address 3.3.10.11 32 [FW-policy-security-rule-policy_sec_local_untrust] destination-address 3.3.10.12 32 [FW-policy-security-rule-policy_sec_local_untrust] destination-address 3.3.10.13 32 [FW-policy-security-rule-policy_sec_local_untrust] destination-address 9.9.20.20 32 [FW-policy-security-rule-policy_sec_local_untrust] destination-address 9.9.20.21 32 [FW-policy-security-rule-policy_sec_local_untrust] service tcp [FW-policy-security-rule-policy_sec_local_untrust] action permit [FW-policy-security-rule-policy_sec_local_untrust] quit
- 配置Trust到Untrust区域的安全策略,允许企业内网用户访问外网资源。假设内部用户网段为10.3.0.0/24。
[FW-policy-security] rule name policy_sec_trust_untrust [FW-policy-security-rule-policy_sec_trust_untrust] source-zone trust [FW-policy-security-rule-policy_sec_trust_untrust] destination-zone untrust [FW-policy-security-rule-policy_sec_trust_untrust] source-address 10.3.0.0 24 [FW-policy-security-rule-policy_sec_trust_untrust] action permit [FW-policy-security-rule-policy_sec_trust_untrust] quit [FW-policy-security] quit
配置脚本
# healthcheck enable healthcheck name isp1_health_01 destination 3.3.10.10 interface GigabitEthernet1/0/1 protocol tcp-simple destination-port 10001 destination 3.3.10.11 interface GigabitEthernet1/0/1 protocol tcp-simple destination-port 10002 healthcheck name isp1_health_02 destination 3.3.10.12 interface GigabitEthernet1/0/2 protocol tcp-simple destination-port 10001 destination 3.3.10.13 interface GigabitEthernet1/0/2 protocol tcp-simple destination-port 10002 healthcheck name isp2_health destination 9.9.20.20 interface GigabitEthernet1/0/7 protocol tcp-simple destination-port 10003 destination 9.9.20.21 interface GigabitEthernet1/0/7 protocol tcp-simple destination-port 10004 # interface GigabitEthernet1/0/1 ip address 1.1.1.1 255.255.255.0 gateway 1.1.1.254 bandwidth ingress 50000 bandwidth egress 50000 healthcheck isp1_health_01 # interface GigabitEthernet1/0/2 ip address 1.1.2.2 255.255.255.0 gateway 1.1.2.254 bandwidth ingress 50000 bandwidth egress 50000 healthcheck isp1_health_02 # interface GigabitEthernet1/0/3 ip address 10.3.0.1 255.255.255.0 # interface GigabitEthernet1/0/7 ip address 2.2.2.2 255.255.255.0 gateway 2.2.2.254 bandwidth ingress 10000 bandwidth egress 10000 healthcheck isp2_health # firewall zone trust set priority 85 add interface GigabitEthernet1/0/3 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/1 add interface GigabitEthernet1/0/2 add interface GigabitEthernet1/0/7 # sa user-defined-application name UD_tax_system rule name 1 ip-address 8.8.8.8 32 port 20001 # interface-group 0 name ifgrp1 add interface GigabitEthernet1/0/1 add interface GigabitEthernet1/0/2 # multi-interface mode priority-of-userdefine add interface GigabitEthernet1/0/7 add interface-group ifgrp1 priority 2 # security-policy rule name policy_sec_local_untrust source-zone local destination-zone untrust destination-address 3.3.10.10 mask 255.255.255.255 destination-address 3.3.10.11 mask 255.255.255.255 destination-address 3.3.10.12 mask 255.255.255.255 destination-address 3.3.10.13 mask 255.255.255.255 destination-address 9.9.20.20 mask 255.255.255.255 destination-address 9.9.20.21 mask 255.255.255.255 service tcp action permit rule name policy_sec_trust_untrust source-zone trust destination-zone untrust source-address 10.3.0.0 mask 255.255.255.0 action permit # policy-based-route rule name tax_system source-zone trust application app UD_tax_system action pbr egress-interface multi-interface mode priority-of-userdefine add interface GigabitEthernet1/0/7 priority 2 add interface-group ifgrp1 # return