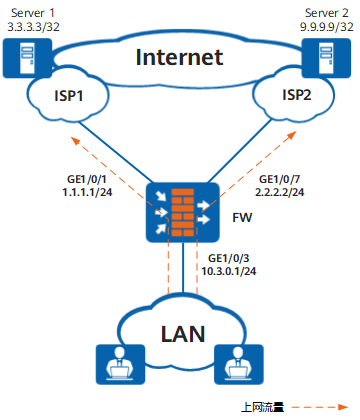
配置策略路由实现多个ISP出接口的智能选路
介绍通过策略路由实现多个ISP出接口智能选路的配置举例。
配置思路
配置ISP选路和策略路由智能选路后,FW可以根据报文目的地址所属ISP网络选择相应出接口。由于生成了ISP路由,所以需要通过策略路由智能选路实现链路的备份或流量的负载分担,智能选路方式为根据链路优先级主备备份。FW需要为两个ISP网络分别创建一条策略路由:ISP1网络对应的策略路由中,目的地址匹配条件为ISP1地址集,且ISP1链路的优先级高于ISP2链路的优先级;ISP2网络对应的策略路由中,目的地址匹配条件为ISP2地址集,且ISP2链路的优先级高于ISP1链路的优先级。这样即可保证其中一条链路故障或过载时,可以使用另一条链路传输后续流量。
- 可选:配置健康检查功能,分别为ISP1和ISP2链路配置健康检查。
-
制作isp1.csv和isp2.csv两个ISP地址文件,将Server 1的IP地址3.3.3.3写入isp1.csv文件中;将Server 2的IP地址9.9.9.9写入isp2.csv文件中,并上传到FW上。

本例着重介绍智能选路相关的配置,其余配置如NAT请根据实际组网进行配置。
操作步骤
- 可选:开启健康检查功能,并为ISP1和ISP2链路分别新建一个健康检查。
<FW> system-view [FW] healthcheck enable [FW] healthcheck name isp1_health [FW-healthcheck-isp1_health] destination 3.3.10.10 interface GigabitEthernet 1/0/1 protocol tcp-simple destination-port 10001 [FW-healthcheck-isp1_health] destination 3.3.10.11 interface GigabitEthernet 1/0/1 protocol tcp-simple destination-port 10002 [FW-healthcheck-isp1_health] quit [FW] healthcheck name isp2_health [FW-healthcheck-isp2_health] destination 9.9.20.20 interface GigabitEthernet 1/0/7 protocol tcp-simple destination-port 10003 [FW-healthcheck-isp2_health] destination 9.9.20.21 interface GigabitEthernet 1/0/7 protocol tcp-simple destination-port 10004 [FW-healthcheck-isp2_health] quit

此处假设3.3.10.10、3.3.10.11和9.9.20.20、9.9.20.21分别为ISP1和ISP2网络中已知的设备地址。
如果健康检查配置完后,状态一直为down,请检查健康检查的配置。
对于V500R001C80之前的版本,需要在FW上配置对应的安全策略,允许FW向目的设备发送健康检查探测报文。对于V500R001C80及之后的版本,健康检查的探测报文不受安全策略控制,默认放行,无需配置相应安全策略。
- 配置接口的IP地址和网关地址,配置接口所在链路的带宽和过载保护阈值,并应用对应的健康检查。
[FW] interface GigabitEthernet 1/0/1 [FW-GigabitEthernet1/0/1] ip address 1.1.1.1 255.255.255.0 [FW-GigabitEthernet1/0/1] gateway 1.1.1.254 [FW-GigabitEthernet1/0/1] bandwidth ingress 50000 threshold 90 [FW-GigabitEthernet1/0/1] bandwidth egress 50000 threshold 90 [FW-GigabitEthernet1/0/1] healthcheck isp1_health [FW-GigabitEthernet1/0/1] quit [FW] interface GigabitEthernet 1/0/3 [FW-GigabitEthernet1/0/3] ip address 10.3.0.1 255.255.255.0 [FW-GigabitEthernet1/0/3] quit [FW] interface GigabitEthernet 1/0/7 [FW-GigabitEthernet1/0/7] ip address 2.2.2.2 255.255.255.0 [FW-GigabitEthernet1/0/7] gateway 2.2.2.254 [FW-GigabitEthernet1/0/7] bandwidth ingress 50000 threshold 90 [FW-GigabitEthernet1/0/7] bandwidth egress 50000 threshold 90 [FW-GigabitEthernet1/0/7] healthcheck isp2_health [FW-GigabitEthernet1/0/7] quit
- 上传ISP地址文件到FW,可以使用SFTP方式进行传输,导入的ISP地址文件固定存放在根目录下名称为isp的文件夹内,具体步骤略。
- 为ISP1和ISP2分别创建运营商名称isp1_ifgrp和isp2_ifgrp,并关联对应的ISP地址文件。
[FW] isp name isp1_ifgrp set filename isp1.csv [FW] isp name isp2_ifgrp set filename isp2.csv
- 为ISP1和ISP2分别新建一个ISP接口组,并将接口加入对应的ISP接口组,缺省下发对应的ISP路由。
[FW] interface-group 1 isp isp1_ifgrp [FW-interface-isp-group-1] add interface GigabitEthernet 1/0/1 [FW-interface-isp-group-1] quit [FW] interface-group 2 isp isp2_ifgrp [FW-interface-isp-group-2] add interface GigabitEthernet 1/0/7 [FW-interface-isp-group-2] quit
- 将接口加入安全区域。
[FW] firewall zone trust [FW-zone-trust] add interface GigabitEthernet 1/0/3 [FW-zone-trust] quit [FW] firewall zone untrust [FW-zone-untrust] add interface GigabitEthernet 1/0/1 [FW-zone-untrust] add interface GigabitEthernet 1/0/7 [FW-zone-untrust] quit
- 配置Local到Untrust区域的安全策略,允许FW向目的设备发送相应的健康检查探测报文。

对于V500R001C80之前的版本,需要在FW上配置对应的安全策略,允许FW向目的设备发送健康检查探测报文。对于V500R001C80及之后的版本,健康检查的探测报文不受安全策略控制,默认放行,无需配置相应安全策略。
[FW] security-policy [FW-policy-security] rule name policy_sec_local_untrust [FW-policy-security-rule-policy_sec_local_untrust] source-zone local [FW-policy-security-rule-policy_sec_local_untrust] destination-zone untrust [FW-policy-security-rule-policy_sec_local_untrust] destination-address 3.3.10.10 32 [FW-policy-security-rule-policy_sec_local_untrust] destination-address 3.3.10.11 32 [FW-policy-security-rule-policy_sec_local_untrust] destination-address 9.9.20.20 32 [FW-policy-security-rule-policy_sec_local_untrust] destination-address 9.9.20.21 32 [FW-policy-security-rule-policy_sec_local_untrust] service tcp [FW-policy-security-rule-policy_sec_local_untrust] action permit [FW-policy-security-rule-policy_sec_local_untrust] quit
- 配置Trust到Untrust区域的安全策略,允许企业内网用户访问外网资源。假设内部用户网段为10.3.0.0/24。
[FW-policy-security] rule name policy_sec_trust_untrust [FW-policy-security-rule-policy_sec_trust_untrust] source-zone trust [FW-policy-security-rule-policy_sec_trust_untrust] destination-zone untrust [FW-policy-security-rule-policy_sec_trust_untrust] source-address 10.3.0.0 24 [FW-policy-security-rule-policy_sec_trust_untrust] action permit [FW-policy-security-rule-policy_sec_trust_untrust] quit [FW-policy-security] quit
- 配置对应于ISP1网络的策略路由智能选路,目的地址为ISP1对应的ISP地址文件,使访问Server 1的报文优先从ISP1链路转发。
出接口选择ISP接口组isp1_ifgrp,并指定优先级为2,选择ISP接口组isp2_ifgrp,并指定优先级为1。
[FW] policy-based-route [FW-policy-pbr] rule name isp1_pbr [FW-policy-pbr-rule-isp1_pbr] ingress-interface GigabitEthernet1/0/3 [FW-policy-pbr-rule-isp1_pbr] destination-address isp isp1_ifgrp [FW-policy-pbr-rule-isp1_pbr] action pbr egress-interface multi-interface [FW-policy-pbr-rule-isp1_pbr-multi-inter] mode priority-of-userdefine [FW-policy-pbr-rule-isp1_pbr-multi-inter] add interface isp isp1_ifgrp priority 2 [FW-policy-pbr-rule-isp1_pbr-multi-inter] add interface isp isp2_ifgrp [FW-policy-pbr-rule-isp1_pbr-multi-inter] quit [FW-policy-pbr-rule-isp1_pbr] quit
- 配置对应于ISP2网络的策略路由智能选路,目的地址为ISP2对应的ISP地址文件,使访问Server 2的报文优先从ISP2链路转发。
出接口选择ISP接口组isp2_ifgrp,并指定优先级为2,选择ISP接口组isp1_ifgrp,并指定优先级为1。
[FW-policy-pbr] rule name isp2_pbr [FW-policy-pbr-rule-isp2_pbr] ingress-interface GigabitEthernet1/0/3 [FW-policy-pbr-rule-isp2_pbr] destination-address isp isp2_ifgrp [FW-policy-pbr-rule-isp2_pbr] action pbr egress-interface multi-interface [FW-policy-pbr-rule-isp2_pbr-multi-inter] mode priority-of-userdefine [FW-policy-pbr-rule-isp2_pbr-multi-inter] add interface isp isp1_ifgrp [FW-policy-pbr-rule-isp2_pbr-multi-inter] add interface isp isp2_ifgrp priority 2 [FW-policy-pbr-rule-isp2_pbr-multi-inter] quit [FW-policy-pbr-rule-isp2_pbr] quit
配置脚本
# isp name isp1_ifgrp set filename isp1.csv isp name isp2_ifgrp set filename isp2.csv # healthcheck enable healthcheck name isp1_health destination 3.3.10.10 interface GigabitEthernet1/0/1 protocol tcp-simple destination-port 10001 destination 3.3.10.11 interface GigabitEthernet1/0/1 protocol tcp-simple destination-port 10002 healthcheck name isp2_health destination 9.9.20.20 interface GigabitEthernet1/0/7 protocol tcp-simple destination-port 10003 destination 9.9.20.21 interface GigabitEthernet1/0/7 protocol tcp-simple destination-port 10004 # interface GigabitEthernet1/0/1 ip address 1.1.1.1 255.255.255.0 gateway 1.1.1.254 bandwidth ingress 50000 threshold 90 bandwidth egress 50000 threshold 90 healthcheck isp1_health # interface GigabitEthernet1/0/3 ip address 10.3.0.1 255.255.255.0 # interface GigabitEthernet1/0/7 ip address 2.2.2.2 255.255.255.0 gateway 2.2.2.254 bandwidth ingress 50000 threshold 90 bandwidth egress 50000 threshold 90 healthcheck isp2_health # firewall zone trust set priority 85 add interface GigabitEthernet1/0/3 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/1 add interface GigabitEthernet1/0/7 # security-policy rule name policy_sec_local_untrust source-zone local destination-zone untrust destination-address 3.3.10.10 mask 255.255.255.255 destination-address 3.3.10.11 mask 255.255.255.255 destination-address 9.9.20.20 mask 255.255.255.255 destination-address 9.9.20.21 mask 255.255.255.255 service tcp action permit rule name policy_sec_trust_untrust source-zone trust destination-zone untrust source-address 10.3.0.0 mask 255.255.255.0 action permit # interface-group 1 isp isp1_ifgrp add interface GigabitEthernet1/0/1 # interface-group 2 isp isp2_ifgrp add interface GigabitEthernet1/0/7 # policy-based-route rule name isp1_pbr ingress-interface GigabitEthernet1/0/3 destination-address isp isp1_ifgrp action pbr egress-interface multi-interface mode priority-of-userdefine add interface isp isp1_ifgrp priority 2 add interface isp isp2_ifgrp rule name isp2_pbr ingress-interface GigabitEthernet1/0/3 destination-address isp isp2_ifgrp action pbr egress-interface multi-interface mode priority-of-userdefine add interface isp isp1_ifgrp add interface isp isp2_ifgrp priority 2 # return
云服务器爆款直降90%
新客首单¥68起 | 人人可享99元套餐,续费同价 | u2a指定配置低至2.5折1年,立即选购享更多福利!